Overall Performance:
Total Score: 45/67 Total Time Spent: 2 hours and 4 minutes
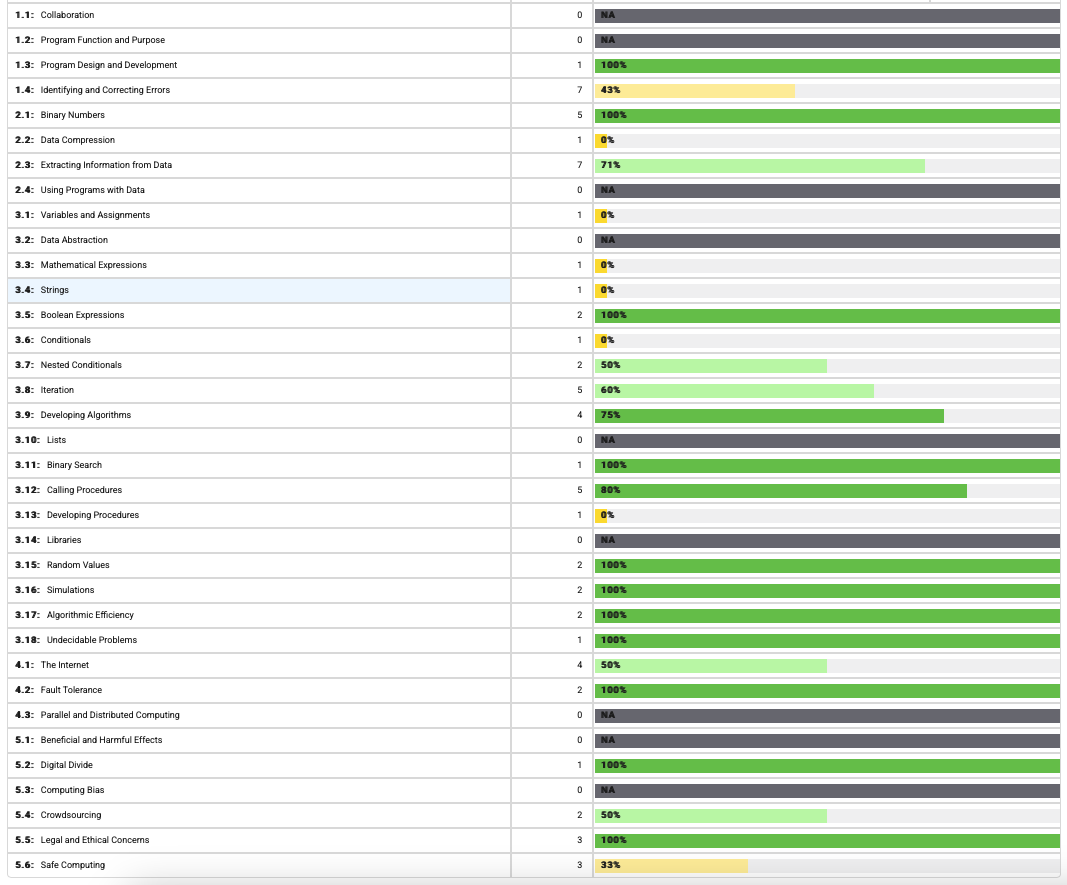
Anlysis:
- Needs improvment in indeitfying vode errors
- Needs imrpovment in speed of indetifcation
- Needs improvment in theory (e.g Data Compression)
- Performed well on efficency questions and simulations
- Perofmred well on ethics and legality
Steps to imrpove:
- Watching College Board Videos and taking notes
- Increasing number of practice, and repition of reviewing questions
- Applying pseudocode to development to gain expiernce with reading and writing
Question Corrections
Q2: A small team of wildlife researchers is working on a project that uses motion-activated field cameras to capture images of animals at study sites. The team is considering using a “citizen science” approach to analyze the images. Which of the following best explains why such an approach is considered useful for this project?
Correct Choice: the image analysis is likely to take a longer time for the research tream than for a distrubuted group of indivudals
Reason: Citizen science is when the general public particpates in the research of a project, and larger groups essentially means less time needed.
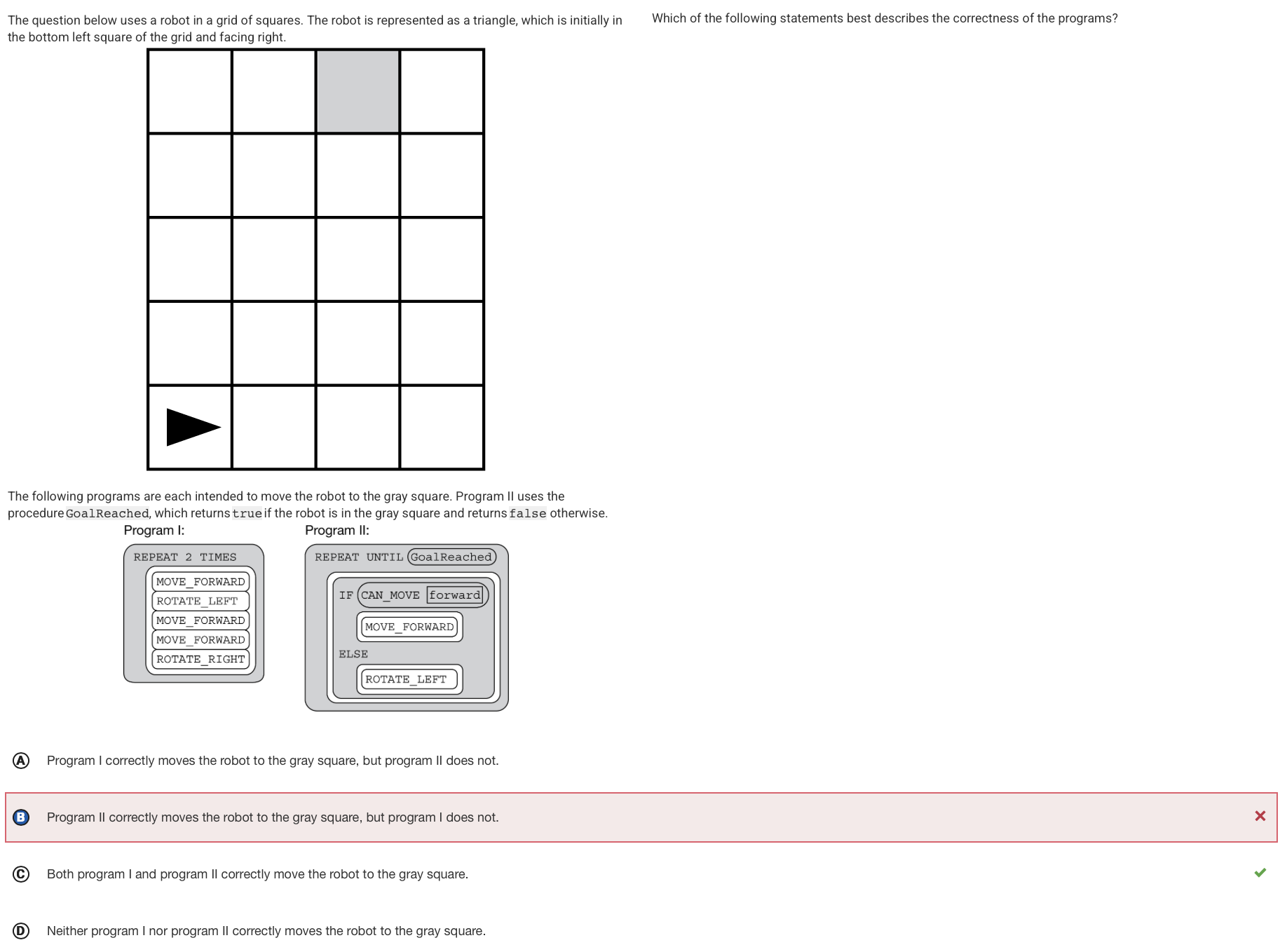 Q6:
Q6:
Reason: Both of them will corectly move to the suare through looking at the repeat cycle and constant repition, and eventually both make it to the end.
Q9: An Internet user has a need to send private data to another user. Which of the following provides the most security when transmitting private data?
Correct Choice: Sending the data using a public encyrption key
Reason: With this key a user can encyrpt any message anf cannot be decrypted without the recievers private key.
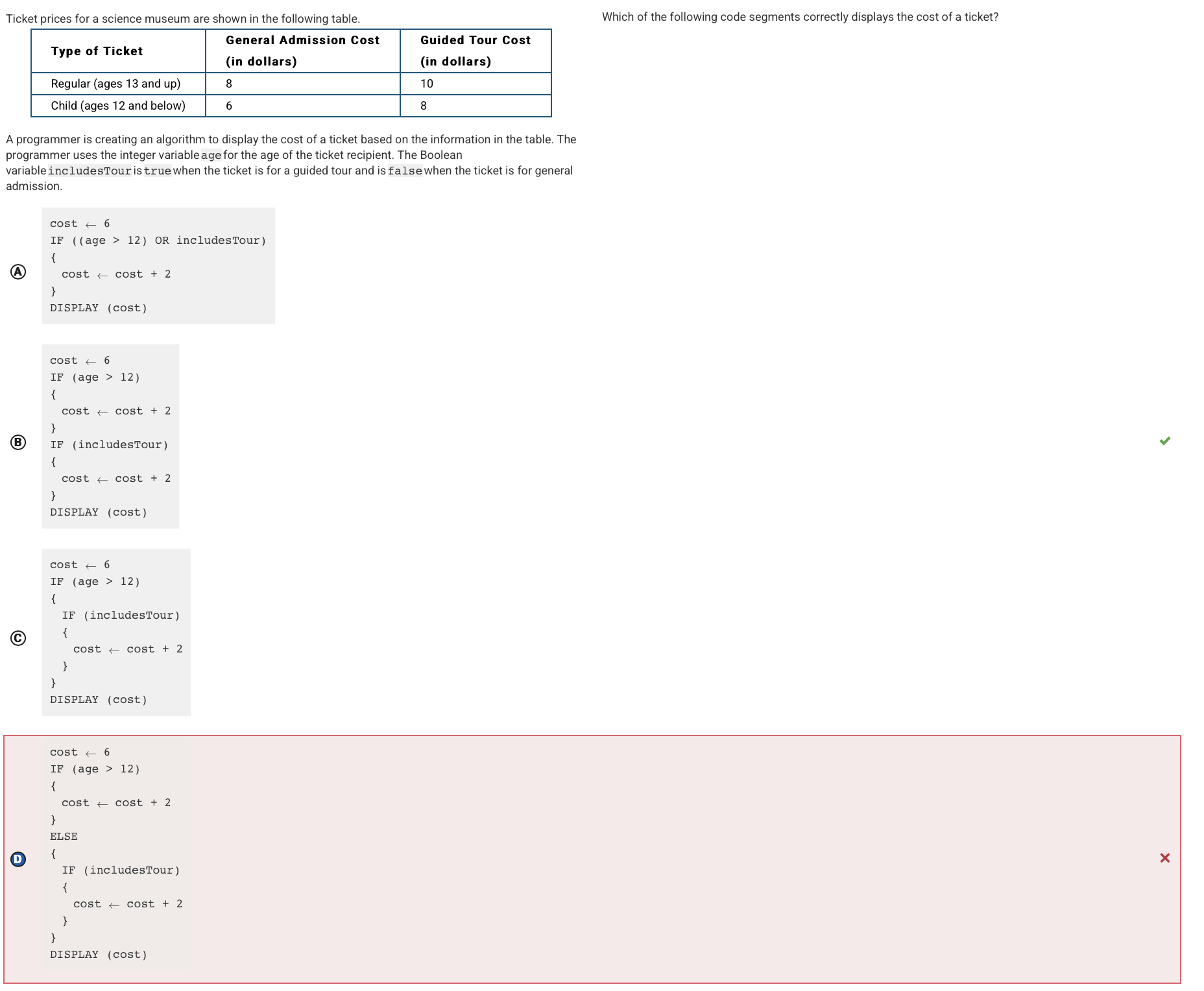 Q10:
Q10:
Reason: This code segment initially sets cost to 6 (the cheapest possible ticket price), then increases cost by 2 for people whose age is greater than 12. Regardless of the person’s age, cost is increased by 2 for people going on a guided tour.
Q14: The following algorithm is intended to take a positive integer as input and display its individual digits in order from right to left. For example, if the input is 512, the algorithm should produce the output 2 1 5. Step 3 of the algorithm is missing. Step 1: Input a positive integer from the user and store it in the variable number. Step 2: Divide number by 10 and record the integer quotient and the remainder. The integer quotient is the quotient with any part after the decimal point dropped. For example, when 127 is divided by 10, the quotient is 12.7, the integer quotient is 12 and the remainder is 7. Step 3: (missing step) Step 4: Repeat steps 2 and 3 until number is 0.
Correct Choice: Step 3: Display the remainder of number divided by 10 and store the integer quotient in number.
Reason: By using integer divison on the number, and then printing the remainder until 0, it will correctly store the information, then terminate itself.
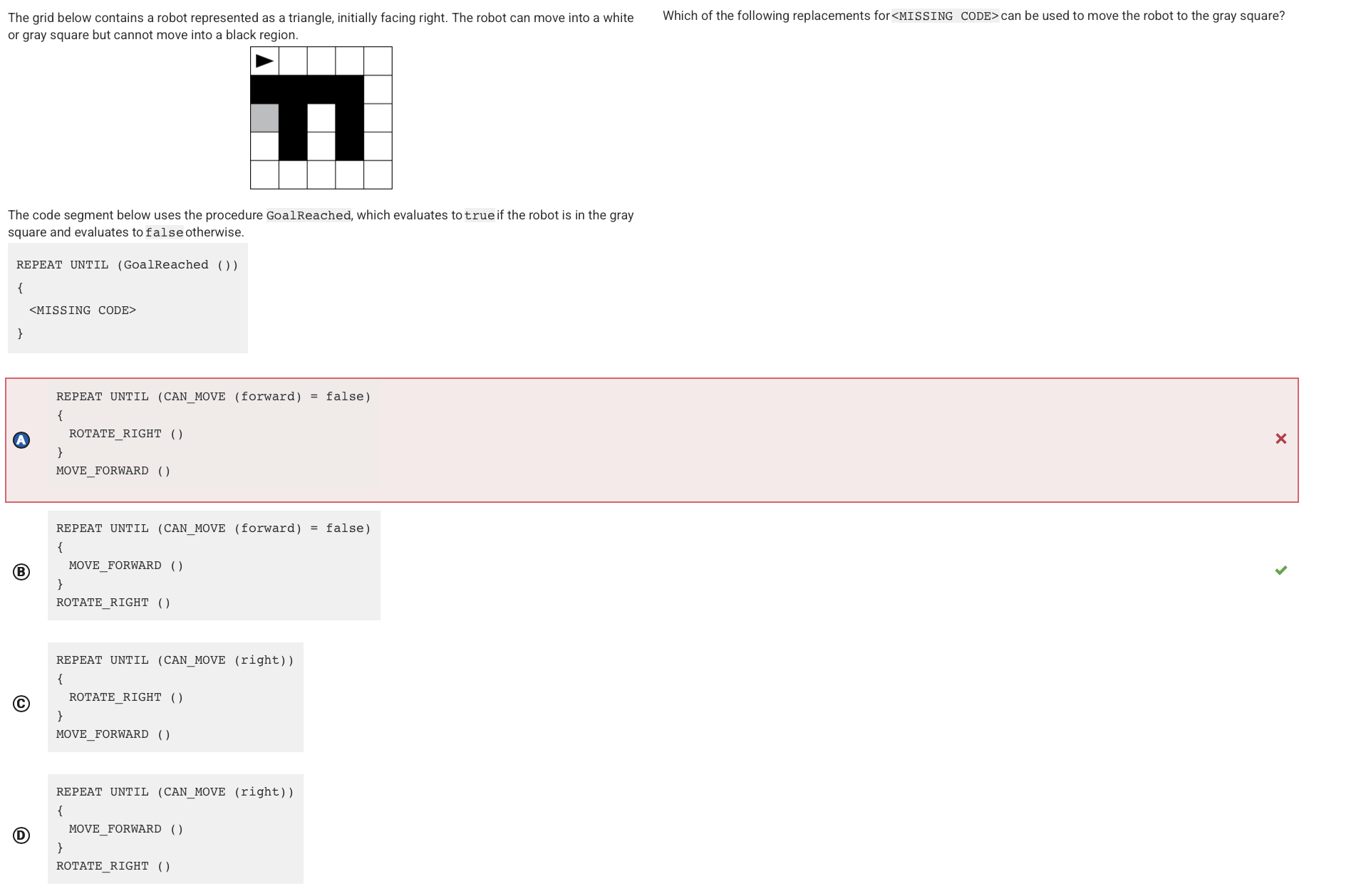 Q18:
Q18:
Reason: This code segment moves the robot forward whenever there is an open square in front of it. Once there is not an open square in front of it, the robot rotates right. The robot moves forward from its initial location to the upper right corner of the grid, then rotates right, then moves forward to the bottom right corner of the grid, then rotates right, then moves forward to the bottom left corner of the grid, then rotates right, then moves forward two squares to the gray square.
Q25:
Which of the following statements correctly explain how the Internet is able to facilitate communication at a large scale?
A central monitoring computer is used to track and maintain the connections of the Internet. Data is routed between points in multiple ways so that if a connection fails, the data can be rerouted around the inoperative connections. Protocols for packets and routing are used so that computers from different manufacturers can communicate in a standard way.
Correct Choice: II and III only
Reason: The Internet is not controlled from a central device. Statements II and III are true. The Internet uses redundant routing to support fault tolerance. The Internet uses protocols so that data is transmitted in a standard format.
Q26:
A list of binary values (0 or 1) is used to represent a black-and-white image. Which of the following is LEAST likely to be stored as metadata associated with the image?
Correct Choice: A duplicate copy of data.
Reason: Metadata typically consists of descriptive information about the data, not a copy of the data itself.
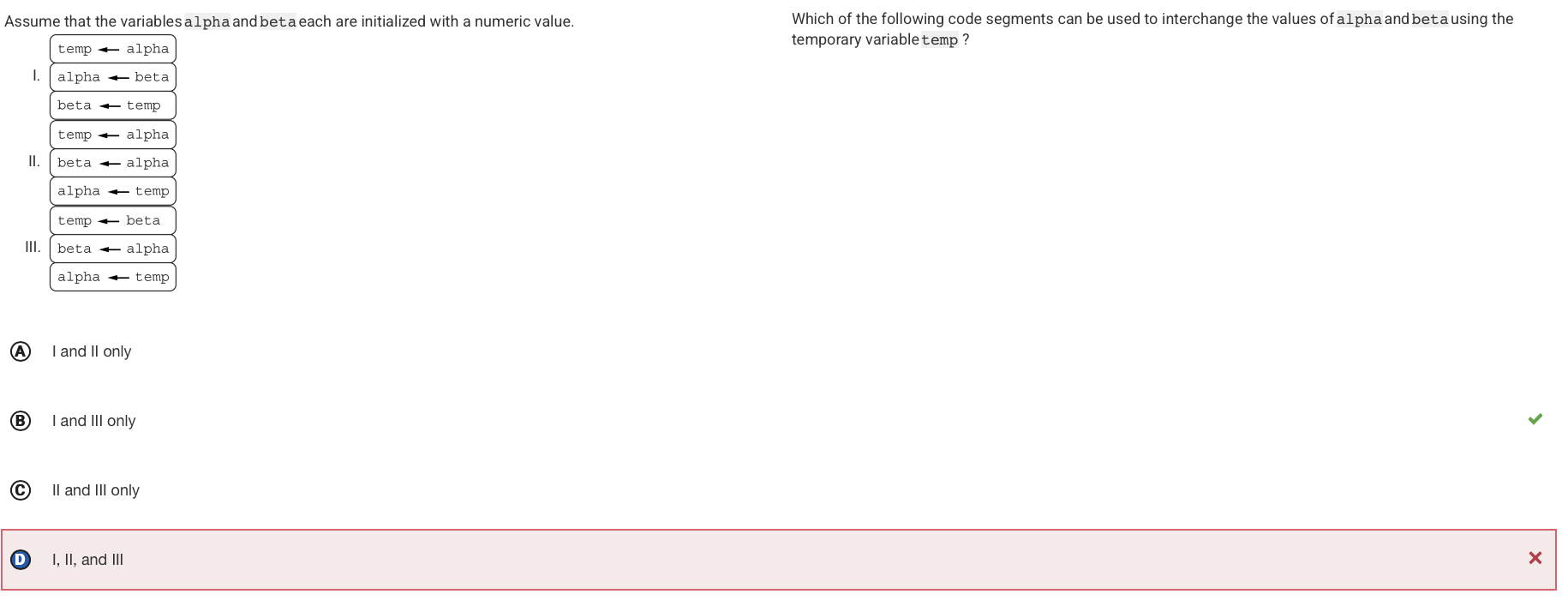 Q28:
Q28:
Reason: Code segment I assigns the initial value of alpha to temp, then assigns the initial value of beta to alpha. The initial value of alpha, which has been stored in temp, is then assigned to beta. Therefore, the values of alpha and beta are interchanged. Code segment II assigns the initial value of alpha to temp, then assigns the initial value of alpha to beta.
Q29:
A person wants to transmit an audio file from a device to a second device. Which of the following scenarios best demonstrates the use of lossless compression of the original file?
Correct Choice: A device compresses the audio file before transmitting it to a second device. The second device restores the compressed file to its original version before playing it.
Reason: Lossless compression is a technique that allows for complete reconstruction of the original data.
Q35:
A programmer notices the following two procedures in a library. The procedures do similar, but not identical, things. Procedure MaxTwo (x, y) returns the greater of its two integer parameters. Procedure MaxThree (x, y, z) returns the greatest of its three integer parameters.
Correct Choice: Procedure Max (numList), which returns the maximum value in the list of integers numList
Reason: A generalization of this procedure is Max, which takes a list parameter as input to determine the maximum of any number of values.
Q38:
Internet protocol version 6 (IPv6) has been introduced to replace the previous version (IPv4). Which of the following best describes a benefit of IPv6 over IPv4?
Correct Choice: IPv6 allows for a greater number of addresses than IPv4, which allows more devices to be connected to the Internet.
Reason: IPv6 allows for a greater number of IP addresses than IPv4 does, which allows more devices to be connected.
Q40:
Which of the following best explains how a certificate authority is used in protecting data?
Correct Choice: A certificate authority verifies the authenticity of encryption keys used in secured communications.
Reason: Certificate authorities are entities that issue digital certificates, which are used to certify the ownership of public keys.
Q55:
The following algorithm is intended to determine the average height, in centimeters, of a group of people in a room. Each person has a card, a pencil, and an eraser. Step 2 of the algorithm is missing. Step 1: All people stand up. Step 2: (missing step) Step 3: Each standing person finds another standing person and they form a pair. If a person cannot find an unpaired standing person, that person remains standing and waits until the next opportunity to form pairs. Step 4: In each pair, one person hands their card to the other person and sits down. Step 5: At this point, the standing person in each pair is holding two cards. The standing person in each pair replaces the top number on their card with the sum of the top numbers on the two cards and replaces the bottom number on their card with the sum of the bottom numbers on the two cards. The sitting partner’s card is discarded. Step 6: Repeat steps 3–5 until there is only one person standing. Step 7: The last person standing divides the top number by the bottom number to determine the average height. Which of the following can be used as step 2 so that the algorithm works as intended?
Correct Choice: Step 2: Each person writes their height, in centimeters, at the top of the card and writes the number 1 at the bottom of the card.
Reason: By starting the process by writing a height at the top of the card and writing a 1 at the bottom of the card, the algorithm will work such that the last person’s card will have the sum of the heights at the top and the number of people at the bottom.
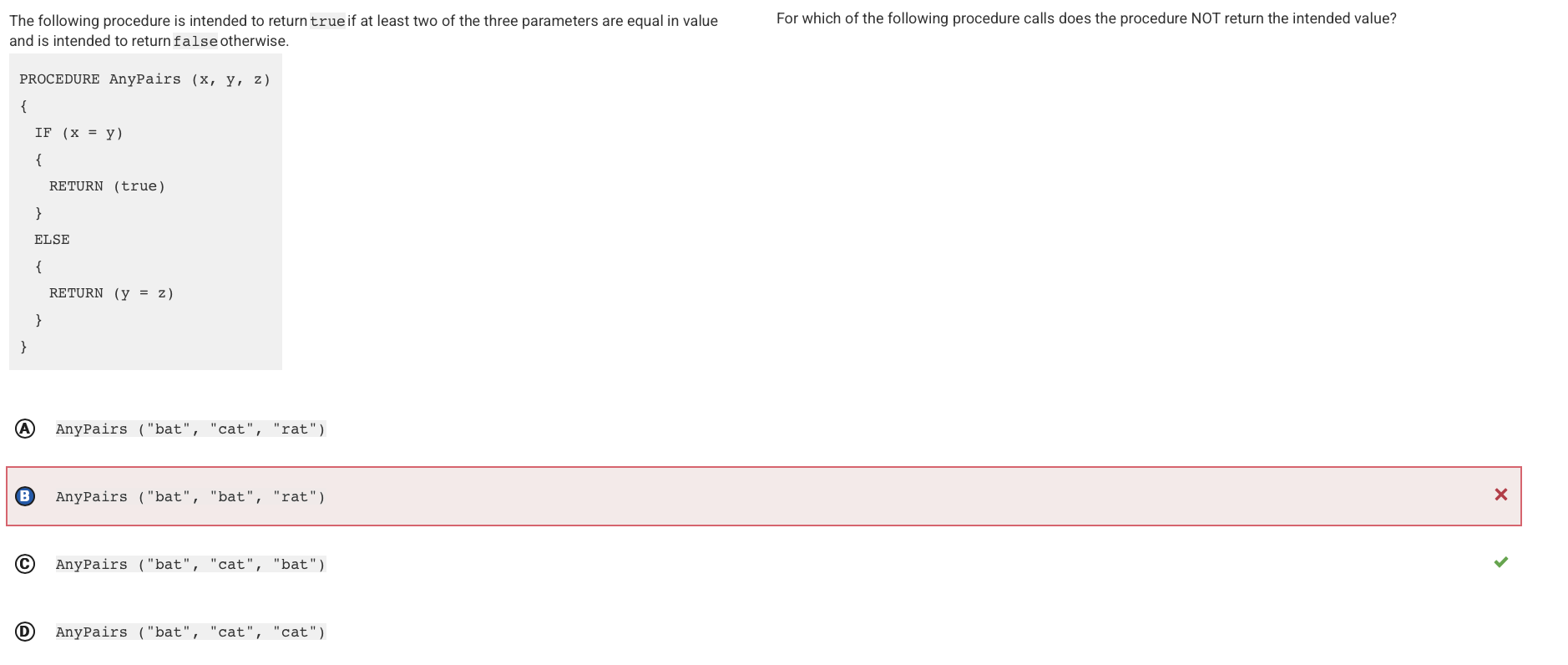 Q58:
Q58:
Reason: The IF condition x = y evaluates to false, so the body of the ELSE statement is executed. The expression y = z evaluates to false, so false is returned.
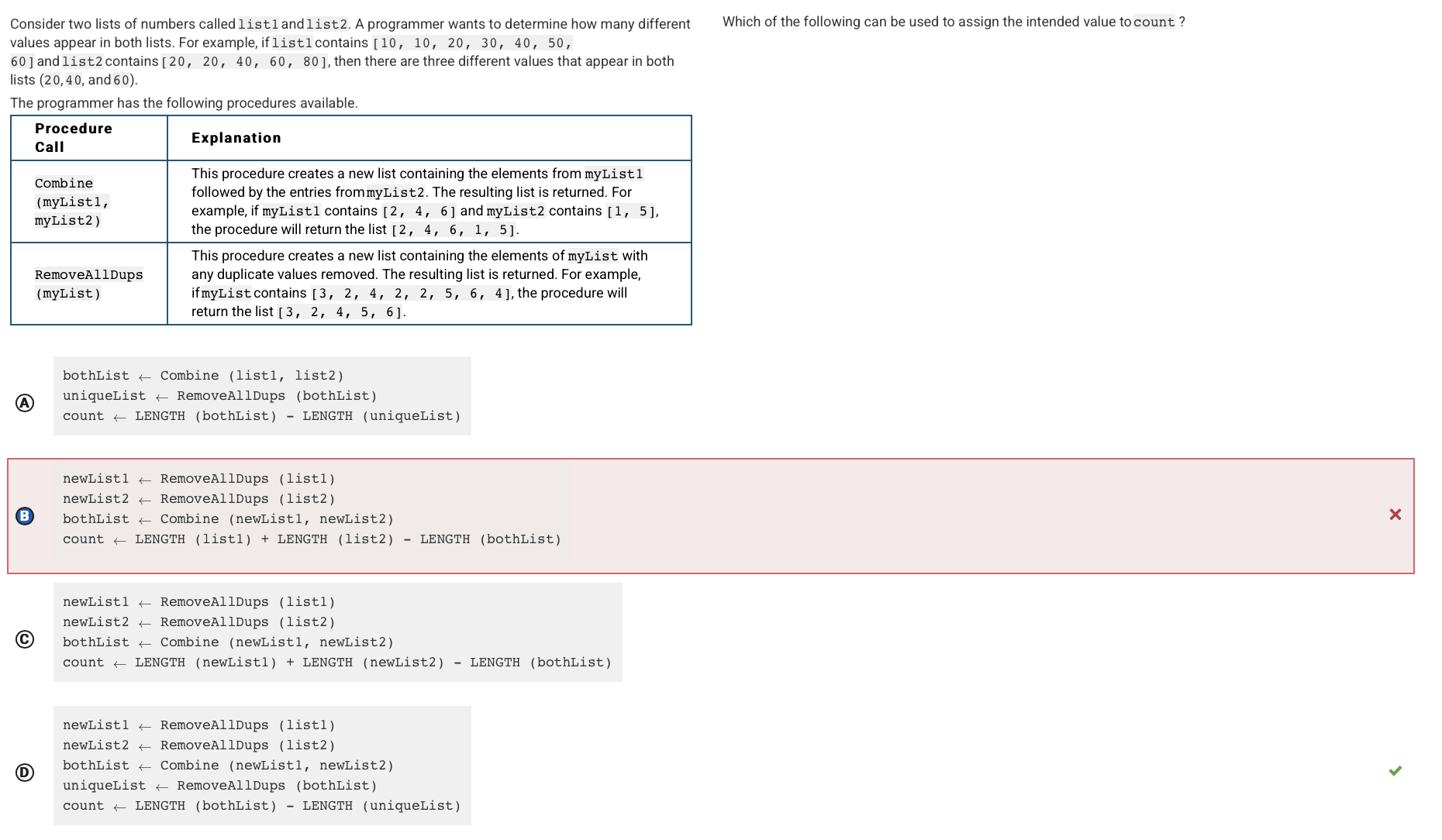 Q60:
Q60:
Reason: The neq list will contain the 5 integers, and the second line of code will creat eht esecond lsit with four integers. The third list, fourth list, and so on, with produce incorrect results of 2.
 Q62:
Q62:
Reason: True is displayed because the IF statement evaluates to true.
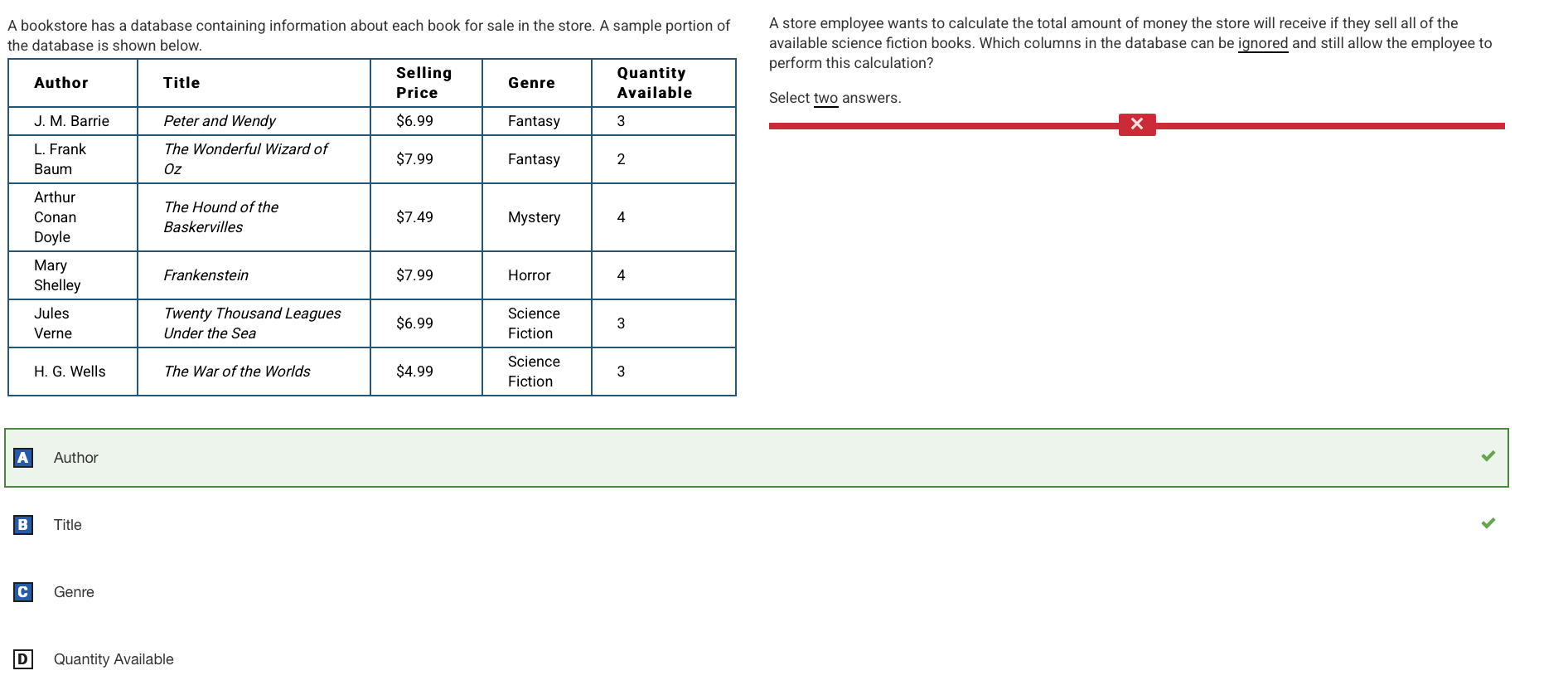 Q63:
Q63:
Reason: Title is also requried because the item that is being sold is required.
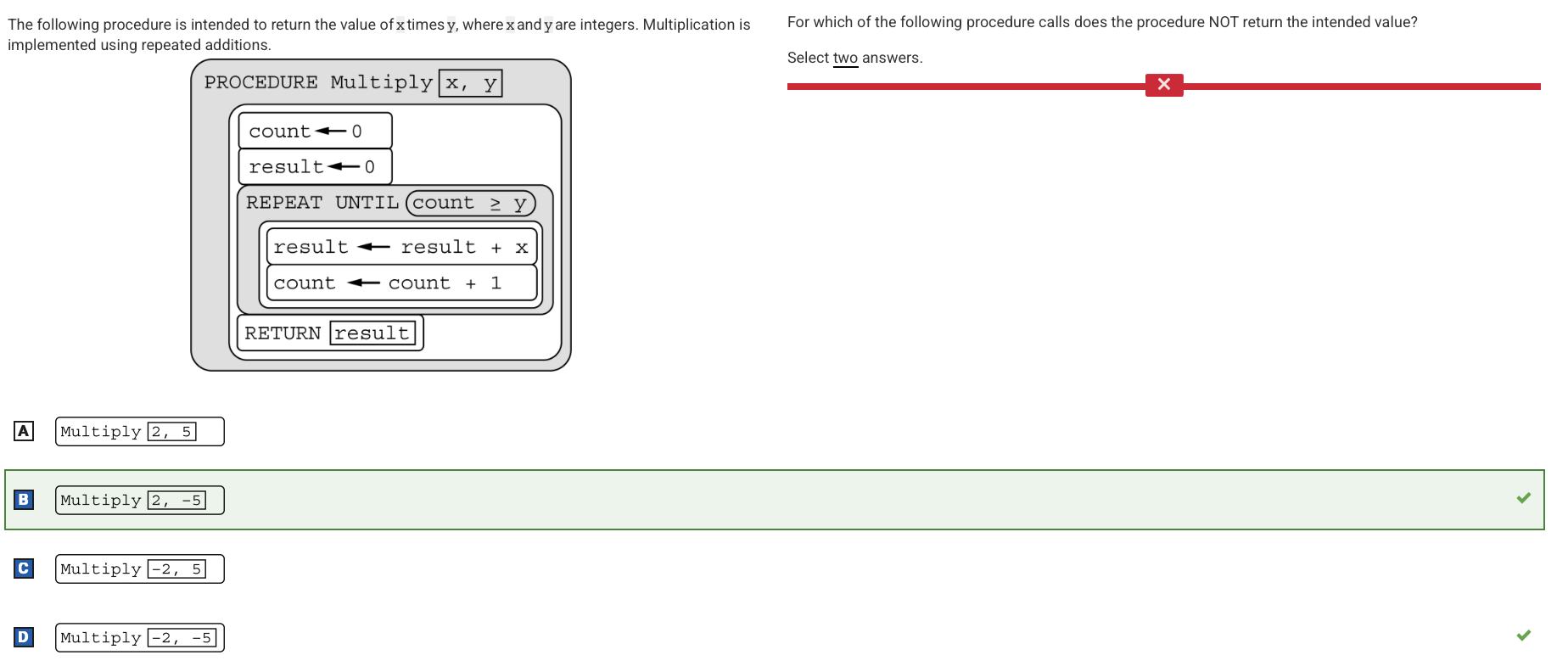 Q64:
Q64:
Reason: Since y is initially negative, the loop condition count ≥ y is initially true, so the body of the loop is never executed and 0 is returned.
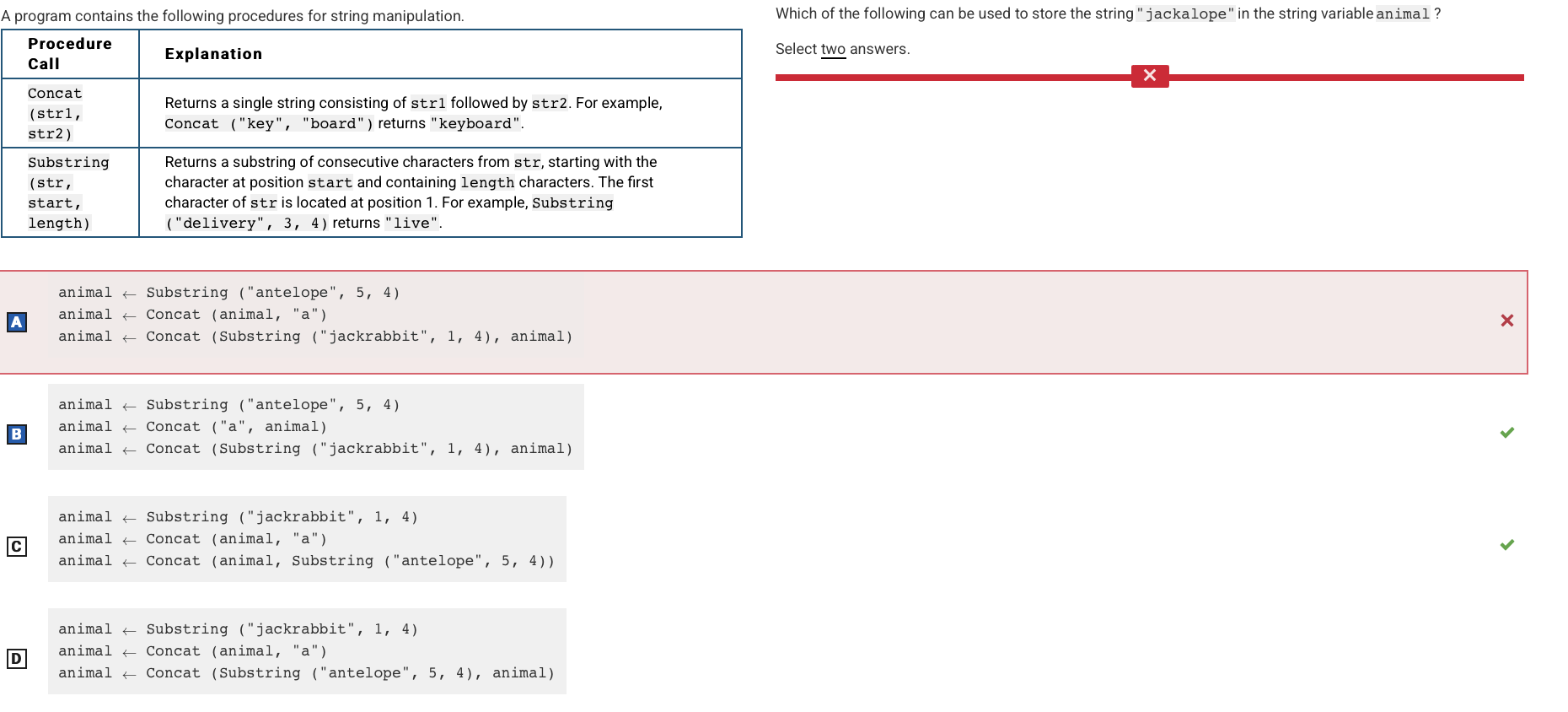 Q65:
Q65:
Reason: Answers B and C are correct because they soeccufcck y can store the animal in the animal string variable, rather than A and D which cannot.
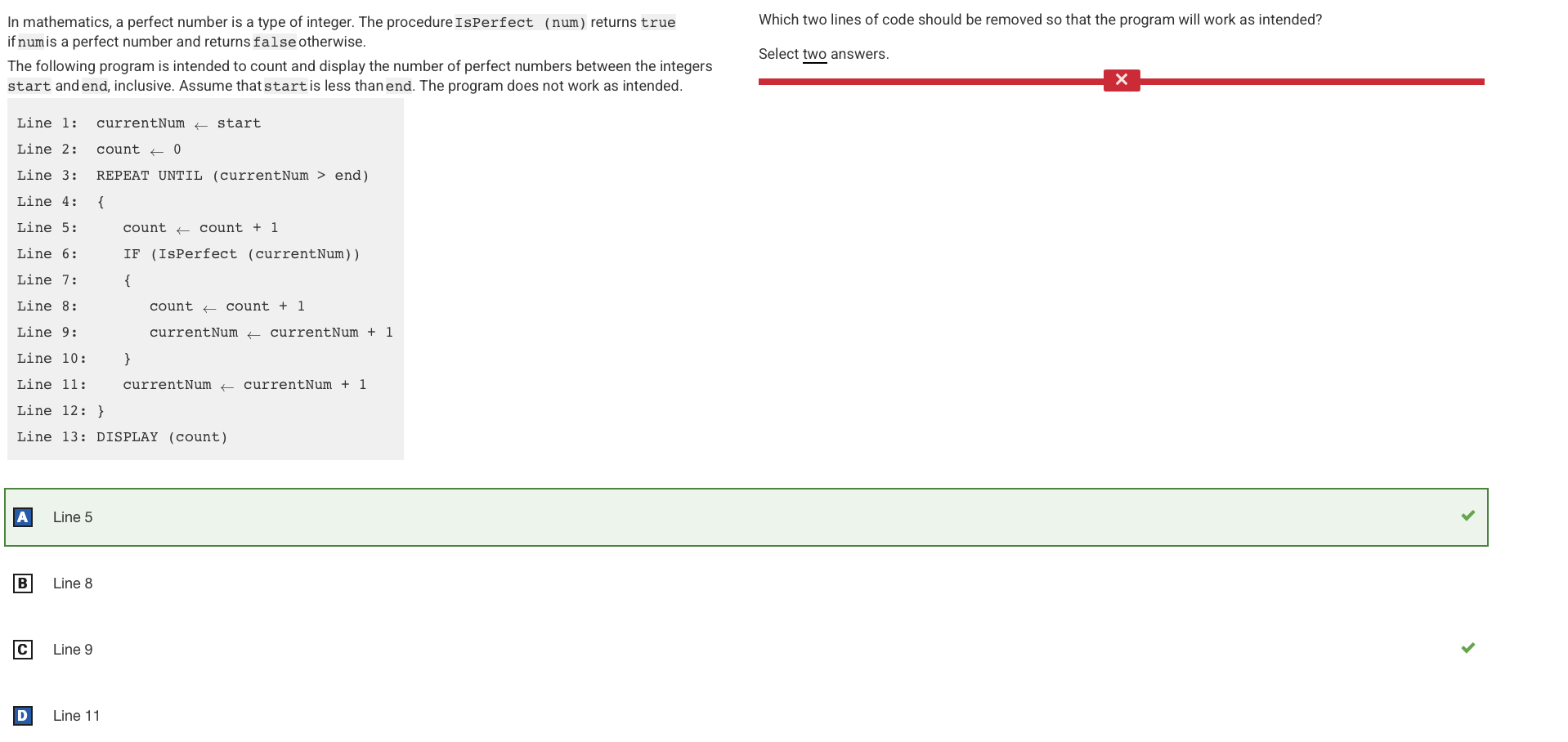 Q66:
Q66:
Reason: This line should be removed. Every integer from start to end should be checked, so currentNum should only be incremented inside the loop but outside the body of the IF statement. So therefore, Line 9 is as well correct.
 Q67:
Q67:
Reason: Regarding Answer B: For this code segment, count is increased to 1 the first time ”maple” is encountered in the list. However, count is reset to 0 when the code segment moves to the next list element. This causes the procedure to return 0 instead of the intended result 1.